As hyper-distributed digital systems become increasingly complex, ensuring their security and compliance requires more than manual oversight. Within the ENACT Cognitive Computing Continuum (CCC), the Security Risk Modeller (SRM) emerges as an essential component, enabling automated, ISO-aligned risk assessment of dynamic deployment configurations. By integrating structured modelling, conceptual mapping, and secure communication mechanisms, SRM provides a foundational capability for evaluating security posture across ENACT’s distributed pilots.
A Core Requirement for Secure, Compliant Deployments
The SRM is engineered to perform risk analysis of deployment configurations within ENACT, based on ISO 27005 framework ensuring compliance with ISO 27001. Risk assessment encompasses three core services: the SRM service, the SRM Mapper, and Keycloak, which together ensure the secure auto-loading, validation, and evaluation of risk models.
At the center of this architecture, the SRM service acts as the computational engine. It supports backend loading of models from the ENACT pilots, validates their structure, and calculates risks using a machine-readable configuration. Importantly, SRM analyzes the pilots systems using strong authentication and authorization mechanisms, using access tokens to ensure that only credentialed users may load, inspect, or modify their models. This prevents any unauthorized handling of sensitive risk-related data.
Supporting both synchronous and asynchronous API requests, SRM also offers secure retrieval of risk analysis reports, enabling rapid feedback during iterative deployment design cycles.
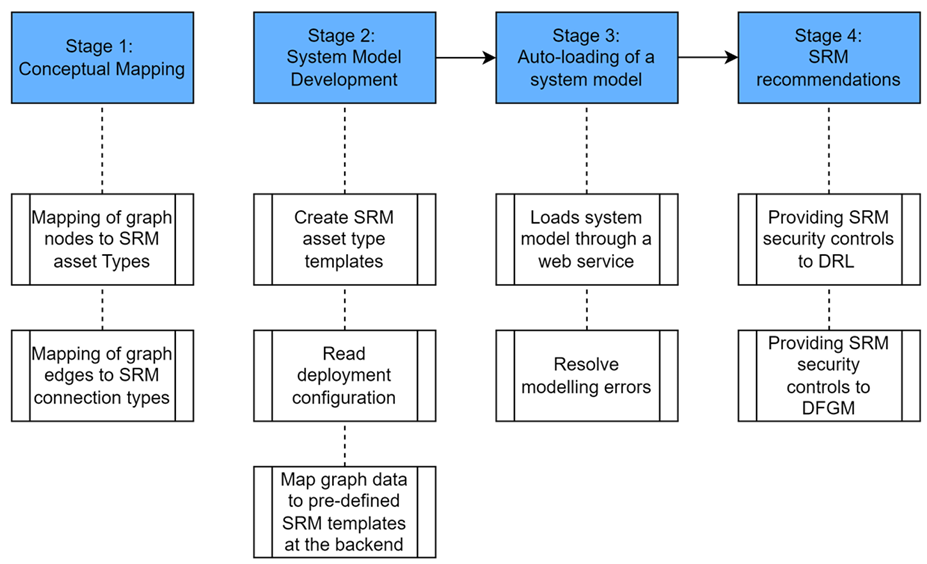
SRM Development Stages
Automated Mapping from Graph Data to Risk Models
To streamline the modelling workflow and reduce the burden on security experts, ENACT introduces the SRM Mapper, a service that converts system configuration graphs into SRM-compliant system models. It processes incoming GEXF files, applies conceptual mapping rules, filters out known issues, and recognizes pre-existing control implementations.
Once mapping is complete, the SRM Mapper automatically communicates with the SRM service to:
- Load the generated model
- Validate its internal consistency
- Perform the associated risk calculations
Depending on the request type, the service returns either an immediate or asynchronous risk report, ensuring flexibility for varied operational needs. Both SRM and SRM Mapper enforce HTTPS-secured, token-authenticated API access, maintaining strict communication security.
SRM also relies on Keycloak for token management and secure communication between services, ensuring that all components of the risk assessment workflow operate within a unified, protected identity and access-management framework.

SRM system model loaded in SRM interface
Integration with ENACT’s AI-Driven Decision-Making
SRM is designed not only to evaluate risk but to support automated decision-making across the CCC. A dedicated SRM instance stores all generated models, enabling downstream components such as the DRL/GNN agent to request risk assessments of optimal deployment configurations.
The workflow follows a clear sequence:
- The DRL/GNN agent submits a configuration graph.
- SRM performs risk analysis and validates the system model.
- SRM outputs a list of required security controls.
- These controls are propagated to the Network Security Policies (NSP) module for runtime enforcement.
This integration ensures that risk is not an afterthought but an embedded dimension of ENACT’s autonomous, adaptive orchestration framework.
Validating SRM Through Real Deployment Configurations
To test and validate automation features, SRM has already been applied to two key scenarios:
- Kubernetes Deployment Configuration
A representative Kubernetes configuration was transformed into a graph consisting of Deployments, Pods, Containers, Replica Sets, and Volumes. From this graph, SRM automatically generated the corresponding system model, demonstrating the feasibility of conceptual mapping and automated model creation.
- Open5GS Deployment Configuration
To emulate pilot conditions more closely, SRM processed an Open5GS deployment configuration, successfully performing automated model loading and validation. Although the resulting system model is visually too large to display in the deliverable, its successful generation confirms SRM’s capacity to support complex, real-world deployment scenarios.
By enabling automated, secure, and standards-aligned risk assessment, the Security Risk Modeller stands as a cornerstone of ENACT’s architecture. Its integration with AI-powered orchestration and its ability to analyses evolving configurations ensure that security remains continuously enforced, supporting a resilient, trustworthy Cognitive Computing Continuum for all ENACT pilots.
